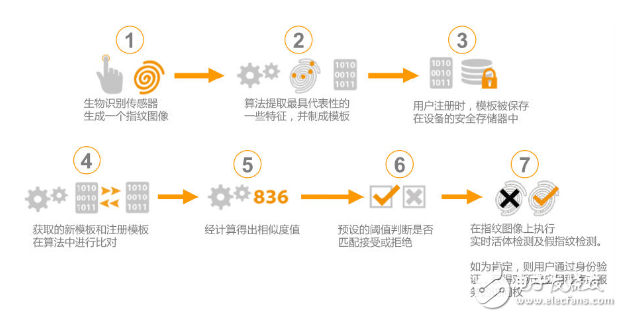
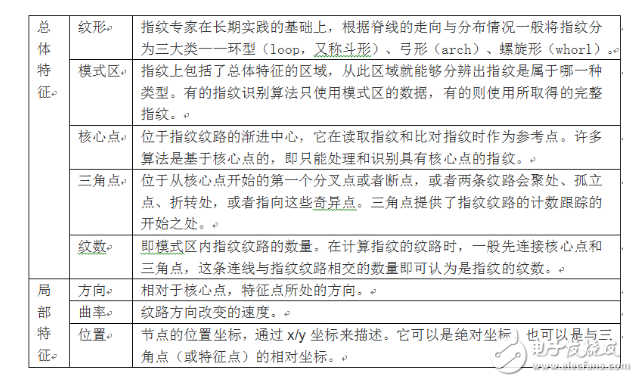
Fingerprints, one of the characteristics of the human body, are called "human identity cards" because of their extremely low repetition rate (about one billionth of a billion). With the popularity of fingerprint recognition technology, especially on mobile phones, this technology used in the field of criminal investigation has now been commercialized. The technology that has been on the high level has begun to be closely related to our lives. Since this technology has been so persecuted to our lives, it is necessary to understand what this "enchanting" is. Today, Xiaobian will talk to you about the things that fingerprint recognition. When it comes to fingerprint recognition technology, in simple terms, its main working process is divided into three steps, namely fingerprint image acquisition, fingerprint image processing and detail matching (Figure 1). First, the human fingerprint is read by a fingerprint identification device (for example, a mobile phone fingerprint identification chip), and the fingerprint image is preprocessed, and then the feature value is extracted to form a feature data model, that is, a template. When the fingerprint is entered again, the "new" fingerprint is compared to the template to calculate the degree of similarity. If the degree of similarity is greater than the set value, unlocking can be achieved. What? Play? Is such a complicated technique summarized by you in a few words? Figure 1 Workflow of fingerprint identification technology Don't worry, Xiaobian is just the most basic three steps of fingerprint recognition. If you want to refine it, you should divide it into 6~7 steps, as shown in Figure 2. Figure 2 Basic principles of fingerprint recognition 1) First, fingerprints are collected by the biometric sensor, and the original image of the fingerprint is preprocessed to obtain a clear fingerprint image. Among them, the segmentation of the fingerprint image is relatively easy to segment the fingerprints collected by some optical instruments, and the segmentation of the fingerprint images collected by some capacitive sensors is difficult. The specific preprocessing and segmentation methods are shown in Table 2. 2) Then, using the fingerprint algorithm to extract some of the most representative features of the fingerprint image to establish a digital representation of the fingerprint (ie, feature data). This is a one-way conversion, that is, it can only be converted from fingerprint images into feature data, but not from feature data to fingerprint images, and thus more secure. In addition, the feature file stores the "detail points" found on the fingerprint image, that is, the bifurcation or tip points of the fingerprint texture, which are often referred to as templates. 3) After the user registers, the template is saved in the secure storage of the device, which will occupy 1KB of storage space. 4) When the user uses the device and inputs the fingerprint, the device uses the algorithm to compare the obtained current fingerprint with the registration template, and calculates the similarity. 5) According to the preset threshold of the algorithm, determine whether the fingerprint matches, and then decide whether to allow the authentication. If the similarity is higher than the preset threshold, the authentication is passed; if the similarity is lower than the preset threshold, the authentication fails. 6) Fingerprint recognition has been basically completed in the fifth step, and the fake fingerprint recognition technology is another supplement to the fingerprint recognition technology (described in detail later). From the work process of fingerprint recognition, we can see that fingerprint recognition is actually a process of comparing fingerprints twice. Since human fingerprints are unique, fingerprint recognition becomes “very simpleâ€. In fact, because the template is part of the identification of the registered fingerprint, and although the human fingerprint is unique, the fingerprint and the registered fingerprint are not completely matched in order to avoid the security of the fingerprint recognition and enhance the fingerprint. The recognition rate and threshold setting are especially important. At the same time, error filtering is another important factor. Before introducing the error filtering of fingerprint recognition, it is still necessary to clarify some basic concepts about fingerprint characteristics. The fingerprint lines are not continuous, smooth and straight, but often interrupted, bifurcated or turned. These breakpoints, bifurcation points, and turning points are called "feature points." The feature points provide confirmation information about the uniqueness of the fingerprint. The most typical ones are the endpoints and the bifurcation points. This is also the feature point that the fingerprint recognition algorithm generally chooses to extract. Others include divergence points, isolated points, ring points, and short points. Grain and so on. In order to facilitate everyone's understanding, Xiaobian here directly gives a table to describe the basic fingerprint features, as shown in Table 1, of course, there is no need to remember these concepts, as long as you see what is going on. Table 1 Basic concepts of fingerprint characteristics
TV speaker:
TV speaker is a kind of speaker unit which is used for LED/LCD televions. TV speakers have loud sound, wide frequency response range and rich bass.
Our main Multimedia Speakers are full ranges speakers units:
1) From the diameter: we have speakers in 1" ~ 3".
2) From the power output, we have speakers of 2W ~ 15W.
FAQ
Q1. What is the MOQ? Led Tv Speaker,Lcd Tv Speaker,Tv Internal Speaker, Tv Speaker Shenzhen Xuanda Electronics Co., Ltd. , https://www.xdecspeaker.com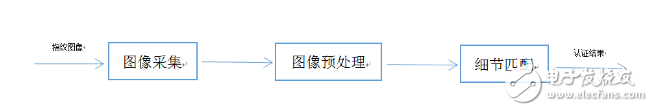


XDEC: 2000pcs for one model.
Q2. What is the delivery lead time?
XDEC: 20 days for normal orders, 15 days for urgent orders.
Q3. What are the payment methods?
XDEC: T/T, PayPal, Western Union, Money Gram.
Q4. Can you offer samples for testing?
XDEC: Yes, we offer free samples.
Q5. How soon can you send samples?
XDEC: We can send samples in 3-5 days.